PART 4: EIGRP Configuration Guide
Enhanced Interior Gateway Routing Protocol
This comprehensive guide explains how to configure Enhanced Interior Gateway Routing Protocol (EIGRP) across different Cisco platforms. I'll cover both traditional numbered mode and modern named mode configurations, along with essential features and verification commands.
Configuration Methods
EIGRP can be configured in two ways in IOS XE:
1. Traditional Numbered Mode (Classic)
R1(config)# router eigrp <AS-NUMBER>
R1(config-router)# network <address> <wildcard-mask>
R1(config-router)# no auto-summaryThe Autonomous System number is critical as it must match between neighboring routers. Unlike other parameter mismatches, AS number mismatches produce no syslog alerts.
2. Named Mode (Modern Approach)
Named mode offers better organization with hierarchical configuration structure, separating interface-specific settings from global process settings.
R1(config)# router eigrp <PROCESS-NAME>
R1(config-router)# address-family ipv4 unicast autonomous-system <AS-NUMBER>
R1(config-router-af)# network <address> <wildcard-mask>
R1(config-router-af)# topology base
R1(config-router-af-topology)# no auto-summaryPlatform-Specific Note: IOS XR only supports named mode configuration and doesn't use the network command—interfaces are added directly to the EIGRP process.
IOS XR:
router eigrp test
address-family ipv4
autonomous-system 65520
Network Advertisement Methods
Using Network Command (IOS XE)
Three approaches to adding networks (Enabling EIGRP on Interfaces):
Specific with wildcard:
network 192.168.1.0 0.0.0.255Activates EIGRP on interfaces within the specified subnet
Without wildcard:
network 192.168.1.0Uses classful boundaries (may activate EIGRP on unintended interfaces)
Shotgun approach:
network 0.0.0.0Activates EIGRP on all interfaces with IP addresses
Using Redistribution (IOS XE)
R1(config-router)# redistribute static # Numbered mode
R1(config-router-af-topology)# redistribute static # Named modeRedistributed routes become external EIGRP routes with an administrative distance of 170.
Advertising Network in IOS XR:
router eigrp test
address-family ipv4
autonomous-system 65520
interface Loopback0
!
interface GigabitEthernet0/0/0/0
!
interface GigabitEthernet0/0/0/2
!
!
!
in IOS XR, just list the interfaces under the address family, and this will enable EIGRP on the interface and advertise that subnet.
Passive Interface Configuration
Passive interfaces continue to advertise their subnets but don't form EIGRP adjacencies:
Legacy IOS & IOS XE:
R1(config-router)# passive-interface GigabitEthernet0/0 # IOS/IOS XE numbered mode
R1(config-router-af-interface)# passive-interface # IOS XR or named modeIOS XR:
router eigrp test
address-family ipv4
interface Loopback0
passive-interface
!
!
!
endThis feature is valuable for:
Connecting to user segments where EIGRP neighbors are unwanted
Reducing unnecessary protocol traffic
Improving security while still advertising networks
Load Balancing with Maximum Paths
EIGRP can load balance traffic sent to a destination across multiple equal-cost paths:
Legacy IOS & IOS XE:
R1(config-router)# maximum-paths <1-32> # Numbered mode in IOS XE
R1(config-router-af-topology)# maximum-paths <1-32> # Named modeIOS XR:
router eigrp test
address-family ipv4
maximum-paths 32
!
!
endThe upper limit varies by platform and IOS version.
Administrative Distance Configuration
EIGRP uses two administrative distance values:
Internal routes (Routes Advertised using Network Command): 90
External routes (Routes Advertised using Redistribtuion Command): 170
To modify these values:
Legacy IOS & IOS XE:
# Change both internal and external AD values:
R1(config-router)# distance eigrp <internal-AD> <external-AD>
R1(config-router-af-topology)# distance eigrp <internal-AD> <external-AD>
# Change AD for specific internal routes only:
R1(config-router)# distance <new-AD> <source-IP> <wildcard> <ACL-number>
R1(config-router-af-topology)# distance <new-AD> <source-IP> <wildcard> <ACL-number>IOS XR:
# Change both internal and external AD values:
router eigrp test
address-family ipv4
distance 60 160
!
!
endNote: The selective distance command only works with internal routes, not external routes. And only Standard ACLs can be used to match the network.
Default Route Advertisement
EIGRP offers three methods to advertise a default route:
1. Using Manual Summarization
Legacy IOS & IOS XE:
# Numbered mode:
R1(config-if)# ip summary-address eigrp <AS-NUMBER> 0.0.0.0 0.0.0.0
# Named mode:
R1(config-router-af-topology)# summary-address 0.0.0.0/0IOS XR:
!! IOS XR Configuration 6.6.2.10I
router eigrp test
address-family ipv4
interface GigabitEthernet0/0/0/0
summary-address 0.0.0.0/0
!
!
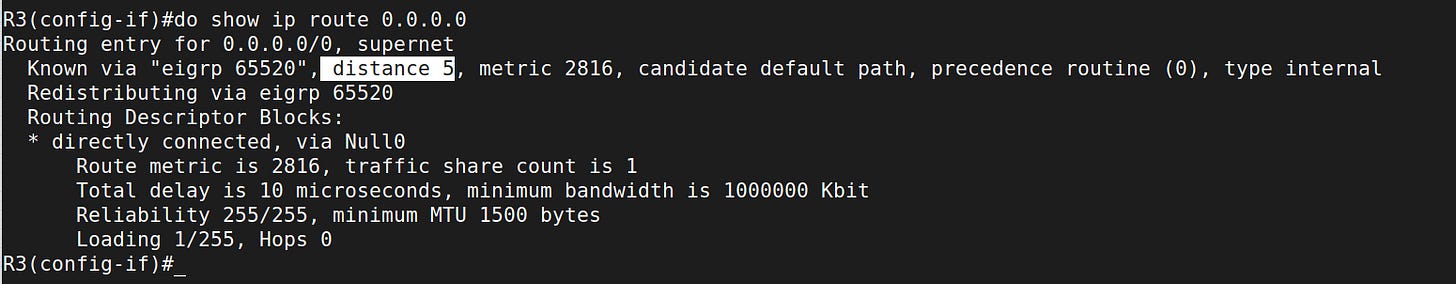
!This approach creates an internal EIGRP default route and automatically adds a local static default route point to null0 interface with AD=5 to prevent loops.
2. Using Redistribution
Legacy IOS & IOS XE:
# Create null route first:
R1(config)# ip route 0.0.0.0 0.0.0.0 null0
# Then redistribute:
R1(config-router)# redistribute static # Numbered mode
R1(config-router-af-topology)# redistribute static # Named modeIOS XR:
! Step 1 : Create a Route Policy to Set the EIGRP Metric
!
route-policy SET_METRIC
set eigrp-metric 10000 100 255 1 1500
end-policy
!
! Step 2 : create static default route pointing to null0
!
router static
address-family ipv4 unicast
0.0.0.0/0 Null0
!
!
! Step 3 : Apply the Route Policy to Redistribution
!
router eigrp test
address-family ipv4
redistribute static route-policy SET_METRIC
!
!
endThis creates an external EIGRP default route (AD=170).
3. Using Network 0.0.0.0 Command (Not Supported in IOS XR)
# Create null route first:
R1(config)# ip route 0.0.0.0 0.0.0.0 null0
# Then add network:
R1(config-router)# network 0.0.0.0 0.0.0.0 # Numbered mode
R1(config-router-af)# network 0.0.0.0 0.0.0.0 # Named modeEIGRP Authentication
EIGRP supports MD5 and SHA-256 authentication algorithms (no clear-text authentication). Authentication is configured at the interface level using key chains:
Legacy IOS & IOS XE:
# Define the key chain:
R1(config)# key chain <name>
R1(config-keychain)# key <number>
R1(config-keychain-key)# key-string <password>
# Apply to interface in numbered mode:
R1(config-if)# ip authentication mode eigrp <AS-NUMBER> md5
R1(config-if)# ip authentication key-chain eigrp <AS-NUMBER> <keychain-name>
# Apply in named mode:
R1(config-router-af-interface)# authentication mode md5
R1(config-router-af-interface)# authentication key-chain <keychain-name>IOS XR:
! Key Chain Configuration
key chain eigrp-auth
key 1
key-string your_secure_password
cryptographic-algorithm md5
send-lifetime 00:00:00 Jan 1 2023 infinite
accept-lifetime 00:00:00 Jan 1 2023 infinite
!
! EIGRP Configuration
router eigrp 100
address-family ipv4 unicast
interface GigabitEthernet0/0/0/0
authentication keychain eigrp-auth
authentication mode md5 ! Use MD5 instead of SHA-256
!
!
!Key chains can be configured with multiple keys and lifetimes for key rotation.
Make sure to double check the IOS Version and the encryption algorithm available based on your IOS version.
Verification and Troubleshooting
Essential EIGRP verification commands:
show ip eigrp neighbors [detail] #IOS & IOS XE
show eigrp neighbors [detail] #IOS XR
show ip eigrp topology [all-links] #IOS & IOS XE
show eigrp topology [all-links] #IOS XR
show ip route [network] #IOS & IOS XE
show route [network] #IOS XR
show ip eigrp interfaces [detail] [interface] #IOS & IOS XE
show eigrp interfaces [detail] [interface] #IOS XR
show interface <interface> | include DLY #IOS & IOS XE
show interface <interface> | include BW #IOS XR
debug eigrp <...>
debug ip eigrp <...>These commands help verify neighbor relationships, examine EIGRP topology information, check routing table entries, and troubleshoot issues with EIGRP operation.
Platform-Specific Considerations
IOS XR: Only supports named mode and may requires different syntax for few commands
IOS XE: Supports both numbered and named modes
Legacy IOS: May have limitations on advanced features like SHA authentication